The hidden risks of shadow IT
BetterCloud
DECEMBER 16, 2024
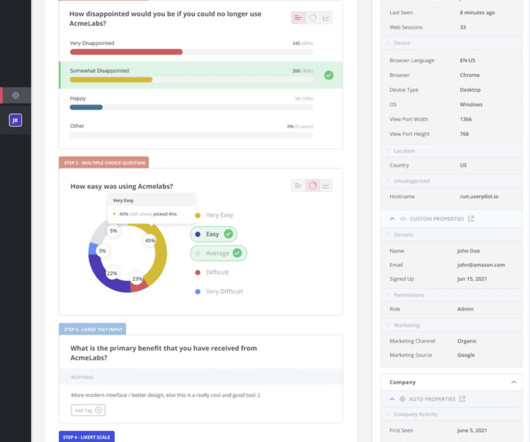
So, as a cautionary tale, its important to understand the hidden risks of shadow IT , including: Operational Security Compliance Financial Remaining unchecked, these four major risks only continue to grow and consequences amplify. Gone are opportunities to share data, collaborate, and find new operational efficiencies.

































Let's personalize your content