Managing infrastructure costs as your company grows
Intercom, Inc.
APRIL 28, 2021
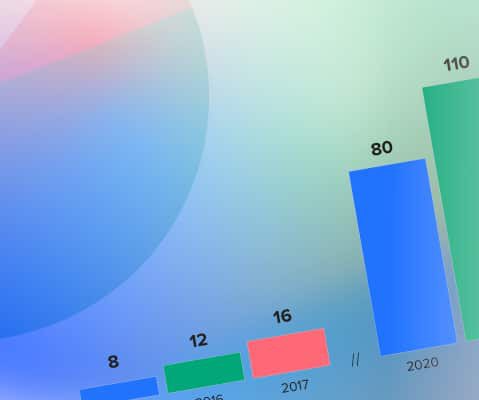
As a result of our reactive strategy, we are gifted with a backlog of cost optimization opportunities. Take the insights from these tools and create a regular review cadence to evaluate, contextualize, and act on any significant fluctuations. Start out small and automate your reporting functionalities and basic cost checks.
















Let's personalize your content