Best DAST tools for DevOps & software development teams
Audacix
APRIL 3, 2023
Table Of Contents The strangest reality of application security in the age of "shift left" is the poor understanding of DAST tools (dynamic vulnerability scanning tools) and, particularly, the value that they the offer as part of a modern software development lifecycle. How does DAST work?
































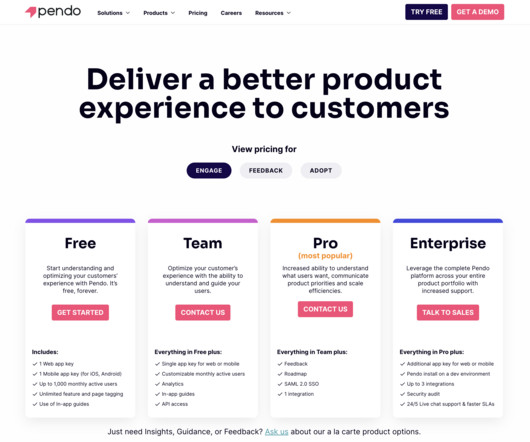












Let's personalize your content